Penetration testing is the practice of finding vulnerabilities in computer systems or networks. The goal is to identify security measures’ weaknesses and exploit them to gain access to sensitive data. This is done through simulated attacks against a target system.
Penetration testing involves processes, tools, and software designed and implemented to simulate attacks and discover potential security vulnerabilities.
Penetration testing, also known as pen testing, involves identifying potential security weaknesses in an organization’s IT infrastructure, such as network devices, software applications, operating systems, firewalls, etc., using various methods to test their effectiveness. Penetration testing is performed to assess the effectiveness of security controls and procedures, and this helps organizations improve their defenses against cyber attacks.
The primary purpose of performing a penetration test is to determine how well you defend your IT assets from external threats. You may be able to detect some of these problems yourself, but it’s often difficult to know what kind of damage could result from a successful attack.
A penetration test allows you to discover where there might be holes in your defenses so that you can take steps to close them before an attacker gets inside.
There are two main types of penetration tests: a white box and a black box.
In white box testing, the tester has complete knowledge of the target environment and understands all aspects of the target’s configuration, internal structure, and any limitations on access.
In black box testing, the penetration testers have no knowledge of the target environment except what they learn during the test. They don’t know anything about the target’s internal network structure, configuration, or any limitations on access, and they only know what they learn while conducting the test.
White box testing is more thorough than black box testing because the tester knows everything about the target environment. However, this type of testing requires a lot of time and resources.
Black box testing is much faster and less resource intensive. Because the tester doesn’t know anything about the environment, they must rely on their skills and experience to determine what to look for.
Penetration testing is usually done by independent consultants who specialize in this area. These security experts typically have extensive training and experience in penetration testing.
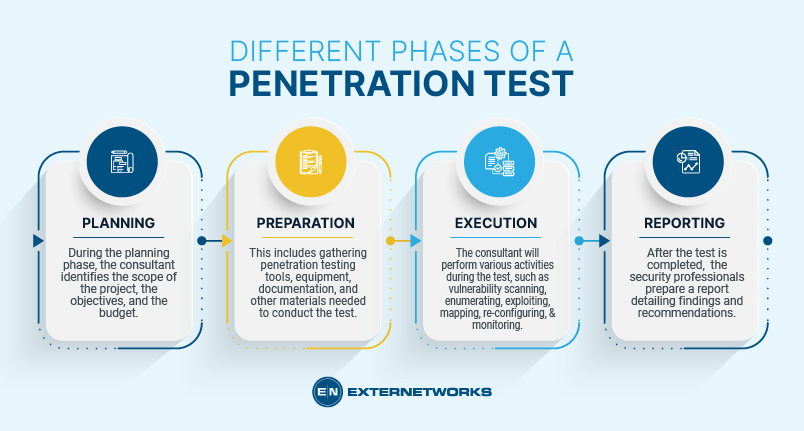
A penetration test has four primary phases: planning, preparation, execution, and reporting.
During the planning phase, the consultant identifies the scope of the project, the objectives, and the budget. The consultant should also identify the target audience and the method of communication.
Once the plan is approved, the consultant begins preparing for the test. This includes gathering penetration testing tools, equipment, documentation, and other materials needed to conduct the test.
The actual test begins once the consultant has gathered all the necessary information. The consultant will perform various activities during the test, such as vulnerability scanning, enumerating, exploiting, mapping, re-configuring, and monitoring.
After the test is completed, the security professionals prepare a report detailing findings and recommendations. This detailed report should include details regarding vulnerabilities, systems affected, and remediation steps taken.
In conclusion, Penetration testing is one of the most effective ways to ensure that your organization’s security protocols are up to par. The best way to do this is by using pen tests from a third-party company that will conduct penetration testing on your behalf. This ensures that all aspects of your target network are tested thoroughly, including firewalls, antivirus software, web servers, email systems, databases, etc.
