Editor’s Note: The article discusses cyber resilience—an organization’s ability to anticipate, withstand, and recover from security incidents. It advocates layered security strategies, proactive planning, and monito... Read More
Cyber resilience measures how well an organization protects itself from cyberattacks. It includes physical and digital security measures, information governance policies, incident response plans, employee training, awareness programs, and processes and procedures designed to protect systems and data from unauthorized access, damage, theft, or loss.
Without a strong cybersecurity framework, organizations are open to attack, where a bad actor might gain access to networks, infrastructures, or personal computer devices, steal sensitive data, and cause significant disruption. This can majorly impact operations, resulting in lost revenue, legal issues, public relations problems, and potential lawsuits.
The goal of any cybersecurity program should be to reduce risk by protecting against threats before they occur. The best way to do this is through prevention, detection, and rapid response. Prevention means preventing attacks from happening in the first place; detection means detecting attacks as soon as possible after they happen, and rapid response means responding quickly to mitigate the effects of an attack once it has been detected.
Cyber resilience is the ability of an organization to continue functioning in a digital world. It’s about adapting and responding quickly when things go wrong, or even better, anticipating problems before they happen. In other words, it’s about having the right people, processes, technology, policies, and culture to ensure that your business can withstand cyber threats and remain operational.
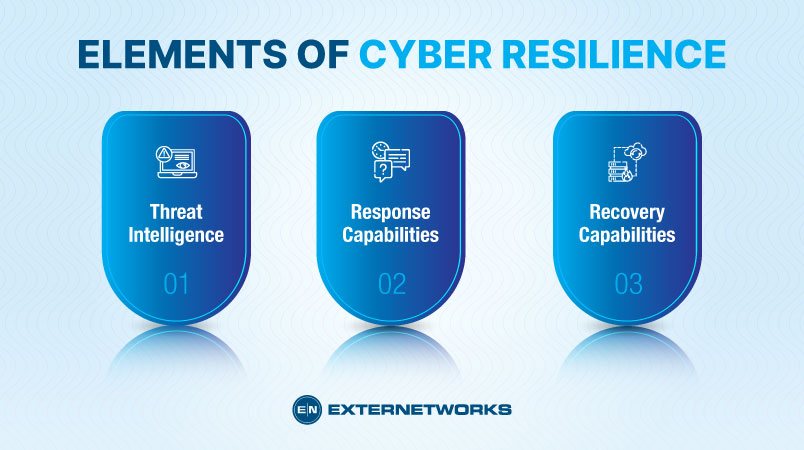
There are three key elements to achieving cyber resilience:
Threat intelligence is collecting, analyzing, and disseminating information on potential threats. The goal is to identify what attackers are doing, where they are coming from, and what vulnerabilities they might exploit.
Response capabilities are the methods an organization uses to detect, prevent, and mitigate threats. This includes everything from firewalls and IDPs to DLP software and antivirus solutions.
Recovery capabilities refer to the procedures an organization uses to restore normal operations after a threat has occurred. This includes everything from disaster recovery plans to backup data and protection against outages.
Cyber resiliency has many benefits, including:
You can reduce the cost of cyber attacks by implementing proper controls at every process stage. You can deploy anti-malware software to scan incoming files before reaching your mainframe. You can also set up an alert system to notify administrators of unauthorized activity. This will help you identify potential threats early and take action before a breach becomes serious.
You can improve productivity by reducing downtime caused by failed hardware or network connections. When employees have access to secure resources, they can focus on their jobs instead of worrying about whether their computer is working properly.
Increased customer satisfaction comes from providing better service and faster response times. Customers appreciate being informed about any changes to your company’s security posture, and they also like knowing that their personal information is safe.
Finally, improving employee morale helps everyone operate more efficiently. Motivating people is easier when they know their efforts are making a difference.
Cyber resilience is the ability of a network to continue operating after being subjected to an attack or other disruptive event. It’s important for any organization that relies on technology, whether a business, government agency, healthcare provider, educational institution or even a non-profit.
The threat landscape has changed dramatically over the past few years. The number and severity of cyber-attacks have increased at an alarming rate. According to Verizon’s 2017 Data Breach Investigations Report, more than 1 million records were compromised daily last year. And according to Gartner Inc., there will be more than 4 billion connected devices by 2020.
The result is that organizations must now consider how to protect themselves from increasingly sophisticated cyberattacks. If left unaddressed, these attacks could cause significant damage to an organization’s reputation, financial stability, customer relationships, and brand image.
The NCSC published a report earlier this week outlining how businesses can improve cyber resilience. The report focuses on four key areas: preparing for attacks, absorbing damage during attacks, recovering quickly and efficiently, and adapting to changes over time.
For example, many cloud providers offer customers access to their infrastructure without requiring them to provide credentials. This makes it easier for hackers to gain access to sensitive information.
In conclusion, cyber resilience is critically important in any organization’s overall cybersecurity strategy. By taking the time to understand and implement these principles, organizations can create a foundation for enduring success in the digital age.
At ExterNetworks, we understand the importance of staying one step ahead in the ever-evolving landscape of cyber threats. With our proactive monitoring services, you can rest easy knowing that potential threats are being identified and addressed before they can impact your organization. Our team of cybersecurity experts brings years of experience to the table, ensuring that your systems are always protected against the latest threats.
We offer customized solutions to fit your unique cybersecurity needs, ensuring you receive the level of protection your organization requires. Additionally, we help keep your organization compliant with industry regulations and standards, giving you peace of mind knowing that your data is secure.
By choosing ExterNetworks for cyber threat monitoring services, you can save on the costs of hiring an in-house security team while benefiting from top-notch protection. Don’t wait until it’s too late—contact ExterNetworks today to learn more about how our services can benefit your organization.