Introduction to NOC and SOC
The rise of digital networks and the increased reliance on complex IT infrastructures have necessitated robust operational and security frameworks to manage and protect these systems. This is where Network Operations Centers (NOCs) and Security Operations Centers (SOCs) come into play. Both NOC and SOC play pivotal roles in maintaining and safeguarding an organization’s IT environment, but they serve distinct functions and require different skill sets. Understanding these differences is crucial for organizations aiming to optimize their IT operations and security posture.

Network Operations Center (NOC): An Overview
A Network Operations Center, commonly abbreviated as NOC, serves as the central hub through which an organization’s IT infrastructure is monitored and managed. The primary role of a NOC is to ensure that the network is performing optimally and without interruption. This involves the constant monitoring of network traffic, detecting potential issues, and responding promptly to minimize downtime. NOCs operate around the clock, providing continuous oversight of network components, including routers, switches, servers, and other critical devices. By leveraging sophisticated monitoring tools and technologies, NOCs are able to identify and address network inefficiencies, ensuring seamless connectivity and operational efficiency.
Moreover, NOCs play a proactive role in network optimization. Through the generation of performance reports and analysis of traffic patterns, they provide valuable insights that aid in enhancing the network’s capacity, speed, and reliability. This proactive approach helps organizations anticipate potential challenges and implement necessary improvements, making NOCs an indispensable aspect of network management.
Security Operations Center (SOC): A Brief Insight
On the other hand, a Security Operations Center, or SOC, is focused on maintaining the security integrity of an organization’s IT assets. The SOC acts as the frontline defense against cybersecurity threats, constantly monitoring for suspicious activities and potential breaches. Unlike the NOC, which handles performance issues, the SOC is dedicated to identifying, analyzing, and responding to cybersecurity incidents.
The SOC relies on advanced threat intelligence tools and systems to detect vulnerabilities and attack vectors, enabling swift incident response and mitigation. Additionally, SOC teams are typically composed of security analysts, specialists, and engineers who work collaboratively to strengthen the organization’s security framework. They conduct regular security assessments and work on enforcing security policies and procedures, thereby contributing to a fortified security infrastructure.
The Importance of Understanding Their Differences
Understanding the differences between NOC and SOC is essential for organizations that aim to maintain a resilient and effective IT environment. While both centers are integral to an organization’s IT strategy, aligning the right resources and processes behind each function is key to maximizing their effectiveness.
A clear demarcation of roles between the NOC and SOC allows for a more organized and efficient approach to managing IT operations and security challenges. It ensures that performance issues do not overshadow security concerns or vice versa. By delineating responsibilities, organizations can allocate the necessary resources to focus on network performance optimization via the NOC and cybersecurity threat management through the SOC.
Furthermore, with the increasing convergence of IT operations and cybersecurity, a comprehensive understanding of both NOC and SOC enables organizations to foster better collaboration and communication between the two functions.
This collaboration enhances the IT infrastructure’s resilience and strength, thereby furthering the organization’s overarching strategic goals.
In light of the evolving digital landscape, the relevance of both NOCs and SOCs continues to grow. Their collaborative efforts not only support the seamless operation of technology systems but also protect the invaluable data that flows through them, reinforcing the backbone of modern business operations.
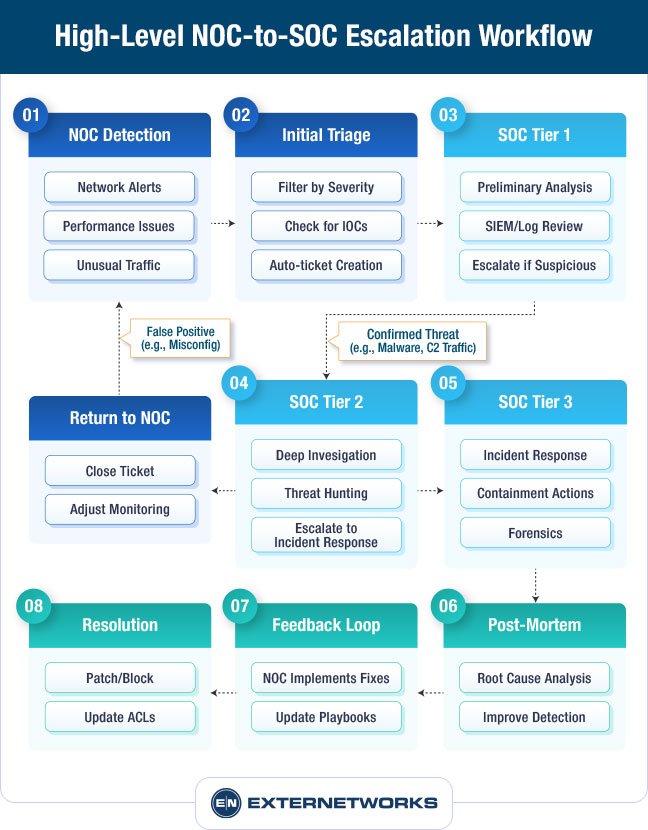
What is a NOC?
A Network Operations Center, commonly abbreviated as NOC, serves as a critical hub in the management and monitoring of an organization’s network infrastructure. It is a centralized location where IT professionals supervise, maintain, and manage the network to ensure its optimal performance. With the rapid evolution of technology and the increasing reliance on digital operations, a NOC plays a vital role in ensuring business continuity and efficiency. To understand its importance, it’s necessary to explore its definition and purpose, key functions, responsibilities, and the common tools and technologies employed.
Understanding the Definition and Purpose of a NOC
A Network Operations Center is the backbone of IT operations, designed to ensure that an organization’s IT services and infrastructure are always running smoothly. The primary purpose of a NOC is to prevent network downtime and to quickly rectify any issues that arise.
By continuously monitoring the network’s health, a NOC helps reduce the risk of outages and minimizes the impact of potential disruptions. Moreover, it assists in managing the organization’s security posture by detecting and responding to potential threats in real-time. Hence, a NOC is not just about surveillance, but also involves proactive management to enhance the overall reliability and security of the network.
Key Functions and Responsibilities of a NOC
Moving beyond its definition, exploring the core functions and responsibilities of a NOC reveals its significance. One of the key functions is continuous network monitoring, which involves overseeing all network activities and identifying irregularities or potential threats.
NOCs are also responsible for providing timely responses to incidents, meaning that any detected issues are promptly addressed through troubleshooting and repairs. Furthermore, they perform routine maintenance tasks such as updating software and hardware, thereby preventing potential vulnerabilities.
In addition to these foundational duties, NOC teams manage network capacity to meet current and future business needs, ensuring performance and security. They also create detailed reports to guide strategic decisions on network improvements or expansions.
Common Tools and Technologies Utilized in a NOC
After examining the functions and responsibilities, it is crucial to delve into the tools and technologies that facilitate the NOC’s efficient operation. NOCs often rely on a range of sophisticated tools and software designed for network performance monitoring, anomaly detection, and incident management.
These tools enable real-time tracking of network traffic, promptly detecting any irregularities or bottlenecks. Technologies such as SNMP (Simple Network Management Protocol) are commonly used for network monitoring, allowing for the effective management of network devices.
In addition, NOCs typically employ advanced analytics and reporting tools that provide deep insights into network health and performance metrics.
Security Information and Event Management (SIEM) systems frequently play a crucial role, enabling the NOC to detect and respond swiftly to security threats.
Moreover, automation tools enhance operational efficiency by handling routine tasks, such as patch management and system updates, thereby allowing NOC personnel to focus on more critical issues.
Thus, as technology becomes increasingly integrated into business operations, the role of a NOC continues to evolve. These centers not only support day-to-day operations but also enable organizations to adapt swiftly to technological advances and emerging security threats.
What is a SOC?
In today’s increasingly digital and interconnected world, cybersecurity has become a paramount concern for businesses and organizations. This is where a Security Operations Center (SOC) plays a crucial role.
A SOC is a centralized unit responsible for monitoring, detecting, and responding to various cybersecurity threats and incidents.
By leveraging cutting-edge technologies and specialized expertise, a SOC helps organizations safeguard their digital assets and maintain a robust security posture.
Definition and Purpose
At its core, a SOC is a dedicated team of cybersecurity experts who work around the clock to protect an organization’s information systems from cyber-attacks.
Their main goal is to detect threats early to reduce the risk of data breaches and security incidents.
A SOC serves as the primary defense, addressing malicious activity swiftly. It not only offers continuous monitoring but also aids strategic planning by analyzing security data and refining strategies to counter evolving threats.
Key Functions and Responsibilities
The functions of a SOC are multifaceted and involve a structured approach to managing security. First and foremost, SOC teams are tasked with continuous security monitoring, which involves overseeing network traffic and system activities to detect suspicious behavior.
When a potential threat is identified, incident response takes center stage; the SOC team assesses the situation, contains the threat, eliminates the risk, and works on recovery efforts.
Moreover, a SOC is responsible for vulnerability management, which entails scanning systems to identify and rectify security weaknesses before adversaries can exploit them.
Another key responsibility is threat intelligence gathering, where the team analyzes internal and external data to predict potential threats, thereby enabling proactive measures.
To support these activities, SOCs often engage in creating and updating security policies, ensuring they align with the latest compliance and regulatory standards.
Common Tools and Technologies Used
To execute its duties effectively, a SOC utilizes a wide array of tools and technologies designed to enhance threat detection and response capabilities.
Among the most essential tools are Security Information and Event Management (SIEM) systems, which provide real-time analysis of security alerts generated by hardware and software.
SIEM solutions enable the SOC team to correlate data from various sources, delivering a comprehensive view of the security landscape.
Next, Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are employed to detect and block potential threats. By analyzing network traffic, these systems help identify unusual patterns that could indicate malicious activity.
Additionally, endpoint detection and response tools (EDR) are crucial for monitoring activities on endpoint devices, quickly identifying threats, and taking corrective actions.
Lastly, the use of advanced analytics and artificial intelligence technologies is becoming increasingly prevalent in SOCs. These technologies contribute to the automation of routine tasks, improving the accuracy of threat detection, and allowing focus on more complex issues.
Through the integration of these tools, a SOC remains agile and responsive in the face of an ever-changing threat landscape.
A SOC combines people, processes, and technology to protect critical infrastructure. Through its approach, it fosters trust and resilience in today’s digital era.
Similarities Between NOCs and SOCs
While Network Operations Centers (NOCs) and Security Operations Centers (SOCs) serve distinct functions within an organization, they also share numerous similarities that facilitate cooperation and enhance overall operational efficiency.
Understanding these commonalities helps in recognizing how these two entities can work harmoniously for a company’s broader technological and security objectives.
Shared Responsibilities and Common Goals
To begin with, NOCs and SOCs have several overlapping responsibilities and shared objectives. Both are crucial in ensuring that an organization’s digital environment remains robust and uninterrupted.
NOCs focus on maintaining network performance and availability, while SOCs prioritize maintaining security and managing threats.
Despite these different focal areas, both centers strive to create a seamless digital experience, ensuring minimal downtime and optimal data protection.
By working towards common goals such as network integrity, service continuity, and data assurance, both centers reduce operational risks that could impact business processes.
Furthermore, the overlap is evident in their monitoring systems. For instance, both NOCs and SOCs deploy sophisticated tools to continuously monitor network activities. While a NOC might mainly monitor these activities to detect performance issues, a SOC will examine the same data for potential security threats.
By aligning their monitoring tasks, NOCs and SOCs can share insights that will fortify both performance and security strategies.
Unified Strategies through Collaborative Efforts
Moreover, the collaboration between NOCs and SOCs is vividly seen in their collaborative efforts in network and security management. By working together, these centers can provide comprehensive coverage against a spectrum of IT challenges—ranging from system failures to targeted cyber attacks.
Collaboration allows for the development of unified strategies that simultaneously address both network operations and security concerns.
Joint efforts also encourage the sharing of expertise and resources, ultimately leading to significant improvements in incident response times and decision-making processes. For instance, when an anomaly is detected, SOCs can offer immediate insights into the security implications, while NOCs can assess the impact on network performance. This coordinated response ensures that issues are addressed swiftly and comprehensively.
Furthermore, cross-training staff from both NOCs and SOCs enriches their skill sets, resulting in a workforce capable of understanding and managing both network and security landscapes. Not only does this promote a more versatile departmental operation, but it also fortifies the organization against evolving cyber threats and network challenges.
Overall, while NOCs and SOCs have unique functions, their similarities and joint efforts build a stronger, more resilient IT infrastructure. The overlapping responsibilities and collaborative initiatives form a foundation that can effectively support and protect an organization’s digital environment.
Key Differences Between NOC and SOC
Understanding the distinctions between a Network Operations Center (NOC) and a Security Operations Center (SOC) is crucial for organizations aiming to protect their digital infrastructure effectively. Although both play pivotal roles in maintaining an organization’s network integrity, they focus on different aspects of system management and require unique skill sets.
Below, we delve into the primary differences between NOC and SOC by examining their focus and objectives, the types of incidents they handle, and the specific skill sets and expertise needed for each.
Focus and Primary Objectives
The primary focus and objectives of a NOC and a SOC define their roles within an organization’s IT ecosystem. NOCs are generally dedicated to ensuring the optimal performance and availability of an organization’s networks and systems.
Their main objectives include monitoring network traffic, managing network resources efficiently, and quickly resolving issues related to system downtime and performance degradation.
Essentially, a NOC is responsible for maintaining network health and ensuring that all systems are running smoothly to support business operations without interruption.
Conversely, a SOC is centered around protecting an organization’s information and assets from cyber threats. Its primary objectives are monitoring for security breaches, detecting unauthorized access, and implementing preventative measures to shield systems from potential attacks. SOCs are tasked with maintaining the overall security posture of the organization, emphasizing security over performance.
Types of Incidents Handled
When it comes to the types of incidents each center handles, the responsibilities of a NOC and a SOC differ significantly. NOCs typically deal with incidents such as equipment failures, network congestion, and power outages. These incidents impact the efficiency and availability of the network, and the NOC is responsible for troubleshooting and resolving these issues promptly.
In contrast, SOCs focus on dealing with cybersecurity incidents like malware attacks, phishing schemes, data breaches, and insider threats. They are equipped to handle a variety of security alerts and threats, conducting investigations and responding to incidents to mitigate any potential damage. Thus, while NOCs handle incidents that impact equipment and network functionality, SOCs are dedicated to addressing security-related challenges.
Skill Sets and Expertise Required
The skill sets and expertise required for professionals in NOC and SOC roles further underscore the differences between the two centers. Personnel working in a NOC typically need a strong background in network engineering, systems administration, and IT operations. They must have the technical skills to address a wide range of network-related issues, including knowledge of routing, switching, and network topology.
On the other hand, SOC personnel require a more specialized set of skills that focus on cybersecurity. This includes expertise in threat analysis, incident response, and knowledge of various security tools and practices. Professionals in a SOC are expected to stay updated on the latest cyber threats and security technologies, which requires continuous learning and adaptation.
In essence, while both NOC and SOC contribute to the smooth functioning and security of an organization’s IT environment, their focus, the nature of incidents they manage, and the competencies required reveal distinct differences in their operational mandates. Appreciating these differences can aid organizations in structuring their IT and security teams effectively to preemptively tackle both network performance and cybersecurity challenges.
The Role of Automation and AI in NOC and SOC
In today’s fast-paced digital world, the integration of Automation and Artificial Intelligence (AI) within both Network Operations Centers (NOC) and Security Operations Centers (SOC) has become not only beneficial but essential. This evolution is driving transformative changes in how these centers operate, manage, and secure vast networks. By streamlining processes and enhancing analytical capabilities, Automation and AI contribute significantly to improving efficiency and security outcomes.
How Automation is Transforming Operations
Automation plays a crucial role in modernizing operations within NOCs and SOCs by significantly reducing manual intervention and simplifying complex tasks. Firstly, automation technologies can handle routine monitoring and maintenance processes, which allows human operators to focus on more strategic and critical issues.
Consequently, this shift minimizes human error and increases productivity. Additionally, automation tools can execute predefined protocols during network anomalies or security threats, which aids in faster incident response and resolution.
Furthermore, the scalability offered by automation allows organizations to scale up their operations without a proportional increase in operational costs. For example, automated systems can efficiently monitor burgeoning network growth amid increased user demand, ensuring consistent performance without the need for additional employees.
Transitioning to centralized dashboards and analytics, automation facilitates a more holistic view of network health and security posture, providing decision-makers with real-time insights and improving their ability to make informed decisions.
AI Applications in Network and Security Management
In parallel, Artificial Intelligence infuses operations with enhanced analytical capabilities, enabling them to predict and respond to changes with unprecedented speed and accuracy.
In NOC environments, AI-driven analytics can predict network bottlenecks and proactively allocate resources to prevent outages. Moreover, machine learning algorithms continuously learn from network activity, fine-tuning performance recommendations and optimizing bandwidth usage based on current data traffic patterns.
When focusing on SOCs, AI is indispensable in fortifying security measures. Its ability to analyze vast amounts of data at incredible speed helps in identifying and prioritizing potential threats. For instance, AI-powered systems can detect anomalous behavior or previously unknown threat patterns, signaling potential breaches far quicker than traditional methods. Additionally, AI tools in SOCs enable threat hunting and intelligence gathering with higher precision, allowing teams to orchestrate effective defense strategies against sophisticated cyber-attacks.
Overall, the emergence of Automation and AI in NOCs and SOCs illustrates a significant leap forward in the operational efficiency and security of organizational networks. Not only do these technologies provide enhanced performance and security, but they also enable organizations to quickly adapt to the ever-changing technological landscape, ensuring sustainable growth and robust systems.
Challenges Faced by NOC and SOC Teams
While Network Operations Centers (NOC) and Security Operations Centers (SOC) are essential components in an organization’s IT infrastructure, they also face a unique set of challenges. These hurdles can impede their effectiveness, but with strategic planning and execution, they can be successfully navigated.
Common Obstacles and Issues in Each Center
One of the primary challenges NOC teams encounter is the high volume of alerts and incidents. These alerts often stem from various network components such as routers, switches, and servers. The sheer volume can lead to alert fatigue, where staff become desensitized to alerts, increasing the risk of missing critical issues.
On the other hand, SOC teams frequently battle sophisticated cyber threats that evolve rapidly. The cybersecurity landscape is in a constant state of flux, making it difficult for SOC specialists to keep up with the latest threats. Moreover, these threats can be highly targeted and employ advanced tactics, requiring continuous vigilance and adaptation.
Both NOC and SOC also face staffing challenges. There is a significant skills gap in the industry, with a shortage of qualified personnel to handle the complex tasks involved effectively. Additionally, retaining skilled staff amid high job demand is a constant concern.
Strategies to Overcome These Challenges
Given these obstacles, it’s crucial for NOC and SOC teams to employ proactive strategies. Firstly, employing advanced monitoring and automation tools can help in filtering and prioritizing alerts, reducing the cognitive load on NOC staff. These tools can also automate routine tasks, allowing human resources to focus on more strategic initiatives.
For SOC teams, continuous training and skill development are key. This not only involves staying updated with the latest cybersecurity trends but also engaging in regular simulations and drills to prepare for potential incidents. Establishing clear communication channels and procedures can also enhance coordination during crises.
In tackling staffing challenges, organizations can invest in fostering a culture of learning and development. Offering competitive compensation, professional growth opportunities, and a positive work environment can help attract and retain top talent. Partnerships with educational institutions and training programs can further bridge the skills gap by creating a pipeline of qualified professionals.
Both NOC and SOC teams must also prioritize cross-functional collaboration. By ensuring seamless exchange of information and coordinated efforts, organizations can create a more resilient security and operational framework.
Thus, while the challenges for NOC and SOC teams are significant, with deliberate strategies and ongoing adaptation, they can not only be managed but also turned into opportunities for strengthening the organization’s IT capabilities.
Choosing the Right Approach for Your Organization
When it comes to selecting the most effective framework for safeguarding your organization’s digital assets, the decision between a Network Operations Center (NOC), a Security Operations Center (SOC), or a combination of both requires careful consideration. The choice is not only about technology but also about aligning with your organization’s unique goals and risk management strategies. To make an informed decision, several critical factors must be assessed.
Key Factors in Choosing Between NOC, SOC, or Both
First and foremost, understanding the primary functions of both a NOC and a SOC is crucial. A NOC focuses on ensuring the optimal performance and uptime of your IT infrastructure, monitoring and managing network issues, and maintaining network health.
Meanwhile, a SOC is dedicated to cybersecurity, protecting your organization from potential threats through constant monitoring and response to security incidents. Deciding between them, or opting for both, largely depends on your organization’s specific needs.
For instance, if your business is heavily reliant on uninterrupted network services, a NOC may be essential. Conversely, if your industry is routinely targeted by cyber threats, investing in a SOC would be a prudent choice. Moreover, for many organizations, the increasingly complex threat landscape makes deploying both centers a necessity rather than an option.
Aligning with Business Goals and Risk Management Strategies
Furthermore, it is imperative that the chosen strategy aligns with your overarching business objectives and risk management frameworks. Efficient operations and robust security must enhance, not hinder, your capacity to achieve business targets.
Begin by examining your organization’s risk profile and tolerance level, assessing how potential network downtimes or security breaches could impact your operations.
Organizations with a higher risk tolerance might prioritize swift recovery capabilities over extensive preventative measures, influencing the choice towards a resource-focused NOC.
On the other hand, companies operating in sectors with strict compliance standards might prioritize sophisticated security safeguards inherent to a SOC.
Additionally, consider the integration of these systems with current business processes. A choice that seamlessly fits into existing workflows without causing disruption is often more beneficial and cost-effective in the long term. Hence, understanding your industry’s regulatory landscape, as well as specific business objectives related to growth, customer satisfaction, or technological advancement, can provide critical guidance in this decision-making process.
Overall, by thoroughly analyzing your organization’s network and security needs and aligning them with your strategic goals and risk management strategies, you can make a choice that not only fortifies your infrastructure but also propels business success.
Cost-Benefit Analysis of Running Separate vs. Combined NOC/SOC Teams
When organizations consider optimizing their IT infrastructure operations, a critical decision point often revolves around how to manage Network Operations Centers (NOC) and Security Operations Centers (SOC). Each plays a distinct role in maintaining the health and security of IT systems, and the decision to run these teams separately or combine them can significantly impact an organization’s efficiency and budget. Here’s a detailed cost-benefit analysis of both approaches.
Separate NOC and SOC Teams
Benefits
- Specialization and Expertise: With separate teams, each can focus on its core competencies. NOC teams can concentrate on maintaining network performance, reliability, and availability, while SOC teams focus on security threats and incidents. This specialization often leads to higher expertise and better performance in each domain.
- Focused Tools and Resources: Separate teams can invest in specialized tools and systems tailored to their unique requirements, such as network monitoring solutions for NOC and threat intelligence platforms for SOC.
- Dedicated Leadership and Strategy: Each team can develop its leadership hierarchy and strategic direction, which allows for clear goals and accountability metrics specific to their operational focus.
Costs
- Increased Operational Costs: Operating separate teams may lead to higher costs due to duplicated resources, including staffing, infrastructure, and software licenses.
- Potential for Silos: Separate teams might develop siloed operations, which can hinder communication and collaboration in addressing complex issues that affect both network performance and security.
Combined NOC/SOC Teams
Benefits
- Cost Efficiency: A combined team can reduce redundancies in software, team staffing, and resource allocation. This integration can lead to significant cost savings and better resource utilization.
- Improved Incident Response: Sharing a team allows for a more comprehensive monitoring of network and security-related issues, often leading to quicker identification and response to incidents that may affect both operations and security.
- Holistic Viewpoint: A unified team fosters a holistic approach to IT operations, aligning performance with security, which improves overall situational awareness and strategic alignment across operations.
Costs
- Resource Strain: Combining teams requires cross-training and additional workload balancing, which might overwhelm staff, especially if team members are expected to gain proficiency in both network and security domains.
- Complexity in Management: Managing a unified NOC/SOC requires robust leadership to integrate operations effectively and ensure neither performance nor security is compromised.
- Blurring of Focus: There is a risk that in trying to cover both areas, the team might lack depth in addressing highly specialized issues, leading to challenges in maintaining expertise.
Key Metrics and KPIs for NOC vs SOC
In the realm of managed IT services, both Network Operations Centers (NOCs) and Security Operations Centers (SOCs) play critical roles in ensuring seamless network performance and robust cybersecurity defenses. However, their functions and focus areas differ, necessitating distinct metrics and Key Performance Indicators (KPIs) to measure their effectiveness. Understanding these core metrics is vital for improving operations and meeting strategic objectives.
Network Operations Center (NOC) Metrics
Mean Time to Resolution (MTTR)
MTTR is a crucial metric for NOCs, reflecting the average time taken to resolve network issues after they have been identified. This metric is essential for evaluating the efficiency and responsiveness of the network team in minimizing downtime and maintaining service quality.
Network Uptime
Network uptime measures the percentage of time that network services are operational. High network uptime is a sign of a well-functioning NOC, demonstrating the ability to preemptively address potential disruptions and maintain consistent service availability.
First Contact Resolution (FCR)
FCR measures the percentage of incidents resolved at the first point of contact without escalation. This metric indicates the competency and effectiveness of NOC staff in handling a wide range of network-related issues promptly.
Change Success Rate
This metric evaluates how often network changes are implemented successfully without causing further issues. A high change success rate underscores the NOC team’s proficiency in managing network configurations and updates efficiently.
Security Operations Center (SOC) Metrics
Mean Time to Detect (MTTD)
MTTD is a critical KPI for SOCs, indicating the average time taken to identify a security threat or anomaly. Shorter detection times enhance the SOC’s capability to respond swiftly, mitigating potential damage.
Mean Time to Respond (MTTR)
Within a SOC, MTTR focuses on the average time taken to respond to and mitigate identified threats. This response metric gauges the speed and effectiveness of threat containment strategies and incident management processes.
False Positive Rate
This metric identifies the frequency of benign activities incorrectly flagged as threats. A low false positive rate signifies a refined and effective threat detection system, reducing unnecessary workload on security teams.
Rate of Security Incidents
Tracking the number and severity of security incidents over time helps SOCs assess the overall security posture and the effectiveness of preventative measures.
Understanding and optimizing these metrics is crucial for both NOCs and SOCs to enhance their operational efficiency and safeguard organizational assets. By focusing on these KPIs, managed IT service providers can ensure high performance and security standards, ultimately delivering exceptional value to their clients.
Third-party Managed Services
Outsourcing to third-party managed services involves utilizing external organizations to handle certain business functions, such as IT, customer support, or HR. Here’s a look at the pros and cons of outsourcing either or both:
Pros of Outsourcing Third-Party Managed Services
Cost Savings
- Reduction in Overhead Costs: Outsourcing can eliminate the need for large in-house teams and the associated costs such as salaries, benefits, and office space.
- Economies of Scale: Service providers often serve multiple clients, which allows them to leverage bulk purchasing and standardized processes to keep costs down.
Access to Expertise
- Specialization: Third-party vendors typically have specialized knowledge and experience that may not be available in-house.
- Up-to-Date Technology: Providers often invest in the latest technologies and tools to maintain competitive advantages.
Focus on Core Competencies
By outsourcing non-core activities, companies can focus more resources and attention on their primary business objectives, potentially increasing efficiency and effectiveness in those areas.
Scalability
Managed services can easily scale operations up or down based on the client’s needs, providing flexibility to deal with changing business demands.
Improved Risk Management
Vendors often have systems in place to manage risks associated with their services, which can include security protocols and compliance with regulations.
Cons of Outsourcing Third-Party Managed Services
Loss of Control
Companies might have less oversight over processes and quality of services compared to managing these functions in-house.
Dependency on the Vendor
Over-reliance on a third party may lead to potential challenges if there are service disruptions or if the provider’s business conditions change.
Hidden Costs
While outsourcing might reduce direct costs, there are often hidden expenses such as transition costs, communication barriers, and termination fees.
Security and Confidentiality Risks
Sharing sensitive information with an external party can pose risks to data security and confidentiality.
Cultural Differences
For international outsourcing, cultural and language differences can lead to miscommunication and misunderstandings.
Quality Issues
The quality of service may not meet internal standards or customer expectations, which can impact satisfaction and brand reputation.
Potential for Reduced Employee Morale
Outsourcing can sometimes lead to job displacement or affect in-house employee morale, especially if it leads to layoffs.
When considering outsourcing, companies should carefully weigh these pros and cons in the context of their specific business needs, goals, and market conditions. Evaluating potential providers thoroughly and maintaining good communication can mitigate some of the downsides.
Conclusion
Recap of Key Differences and Similarities
Reflecting upon the distinctions and commonalities between Network Operations Centers (NOCs) and Security Operations Centers (SOCs) unveils the intricate tapestry of modern IT management. On the surface, both NOCs and SOCs are bastions of system monitoring and optimization, each working tirelessly to ensure the seamless operation and security of digital environments. They both employ sophisticated technology, expert personnel, and complex processes; however, their core functions diverge quite distinctly.
NOCs primarily focus on the availability and performance of the network. They are tasked with monitoring network infrastructure to preempt and resolve issues related to connectivity, bandwidth, and network hardware. On the other hand, SOCs play a pivotal role in safeguarding network integrity by concentrating on security threats. Their operations are more security-centric, involving the detection, analysis, and response to cybersecurity incidents.
While both centers aim for seamless operations, their tools, team structures, and primary goals—smooth performance versus security assurance—represent the most significant contrasting elements. Nevertheless, the overlapping use of data analytics, real-time monitoring, and incident management showcases their similarities, underscoring their complementary roles in IT environments.
Final Reflections on the Importance of NOC and SOC in Modern IT Environments
Without a doubt, NOCs and SOCs are indispensable pillars in today’s dynamic IT landscape. As organizations increasingly rely on digital infrastructure, the roles of these centers have become more critical. They not only ensure uptime and operational efficiency but also safeguard sensitive data against an ever-evolving threat landscape.
Their importance is further emphasized by the interconnected nature of modern businesses, where even a minor network disruption or security breach can have extensive ramifications. By maintaining a vigilant watch, NOCs keep systems running smoothly, while SOCs protect against potential security threats, ensuring business continuity and protecting an organization’s reputation.
As technology advances, NOCs and SOCs create a stronger, resilient, efficient, and secure IT environment.
Their collaboration leads to comprehensive strategies that drive proactive management, enhance resilience against emerging threats, and fine-tune system performance. These capabilities not only support immediate operational needs but also empower organizations to adapt and thrive in an era defined by rapid technological evolution.
Given their critical roles, it is evident that the integration and enhancement of NOC and SOC functions are crucial investments for the future-ready enterprise.
Curious How a NOC or SOC Fits Into Your IT Setup?
Reach out to ExterNetworks for a free consultation.
Contact Us


